Explore the best malware detection tools for SIM, SEM, and SIEM systems. Learn how to protect your network with effective security solutions.
When looking for a decent SEM tool, you need to make sure that certain functions are included in your choice:
That said, let's move on to the top five malware detection and analysis tools for your network.
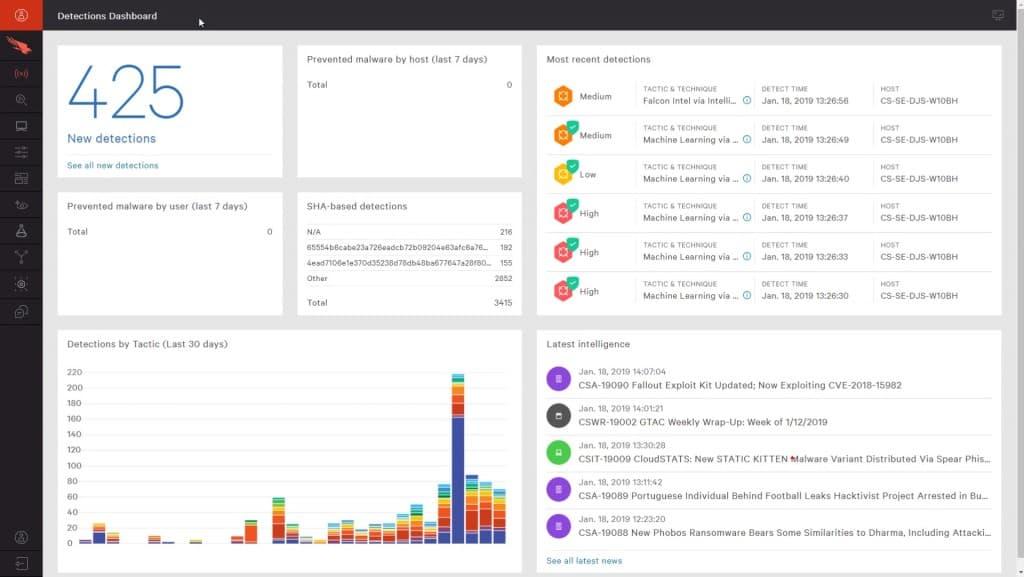
CrowdStrike Falcon is an Endpoint Protection (EPP) platform. It does not operate on network event data, but collects event information on individual endpoints and then transmits it across the network to an analytics engine. As such, it is a SIEM tool. The activity controller is an agent that resides on each protected terminal. The analytics engine resides in the Cloud on the CrowdStrike server. It is therefore a hybrid solution on site/in the cloud.
The EPP is composed of modules and marketed in editions. Each edition has a different list of modules, but all include the Falcon Protect system. Falcon Protect is a next-generation antivirus that monitors processes at an endpoint rather than using the traditional method of analyzing known malware files.
The agent on the terminal composes event logs from process activities and then forwards these records to the CrowdStrike server for analysis. A traditional SEM works with live data. However, Falcon Protect only uses a logging process to gather and transmit events to the analytics engine, so it's live data. It is still an SEM, because it is capable of immediately reporting malicious activity and it does not look for its source in historical records of events.
One of the benefits of separating Falcon Prevent's data collection and analysis processes is that event data is stored for secondary analysis. Operating on live data sometimes makes it possible to miss suspicious activities implemented by manipulating authorized processes. Some malicious activities can only be detected over time by connecting apparently innocent actions that can be akin to a data theft attempt or a sabotage event.
CrowdStrike packages include threat prevention, threat analysis, and device control modules. The basic package is called Falcon Pro and the higher plans are Falcon Enterprise and Falcon Premium. CrowdStrike also offers a managed cybersecurity service called Falcon Complete.
CrowdStrike offers a 15-day free Falcon Pro trial.
CrowdStrike Falcon is our top choice for malware detection and analysis because it brings an innovation to the traditional antivirus model of maintaining a virus signature database. The CrowdStrike Falcon system includes AI methods to detect new viruses and automatically implements blocking procedures. Each new discovery is shared by the entire community of service users, making it possible to quickly deploy antivirus defenses around the world.
Operating system: Windows, Linux, macOS

SolarWinds Security Event Manager (SEM) is a leader in intrusion detection and threat suppression technology solutions. He was previously known as Log & Event Manager (LEM).
To be honest, it is a tool that has everything it takes to ensure the security of a network. It is an SEM that helps network administration and security personnel better detect, respond to, and report on malicious software or suspicious activity, and many people agree with us.
Other features to note:
One point that would make anyone biased toward SolarWinds SEM is the fact that the company doesn't show you the door once you've made a purchase. On the contrary, its support services have been rewarded and continue to help its customers accelerate their business results. You can download SolarWinds Security Event Manager for a free 30-day trial.
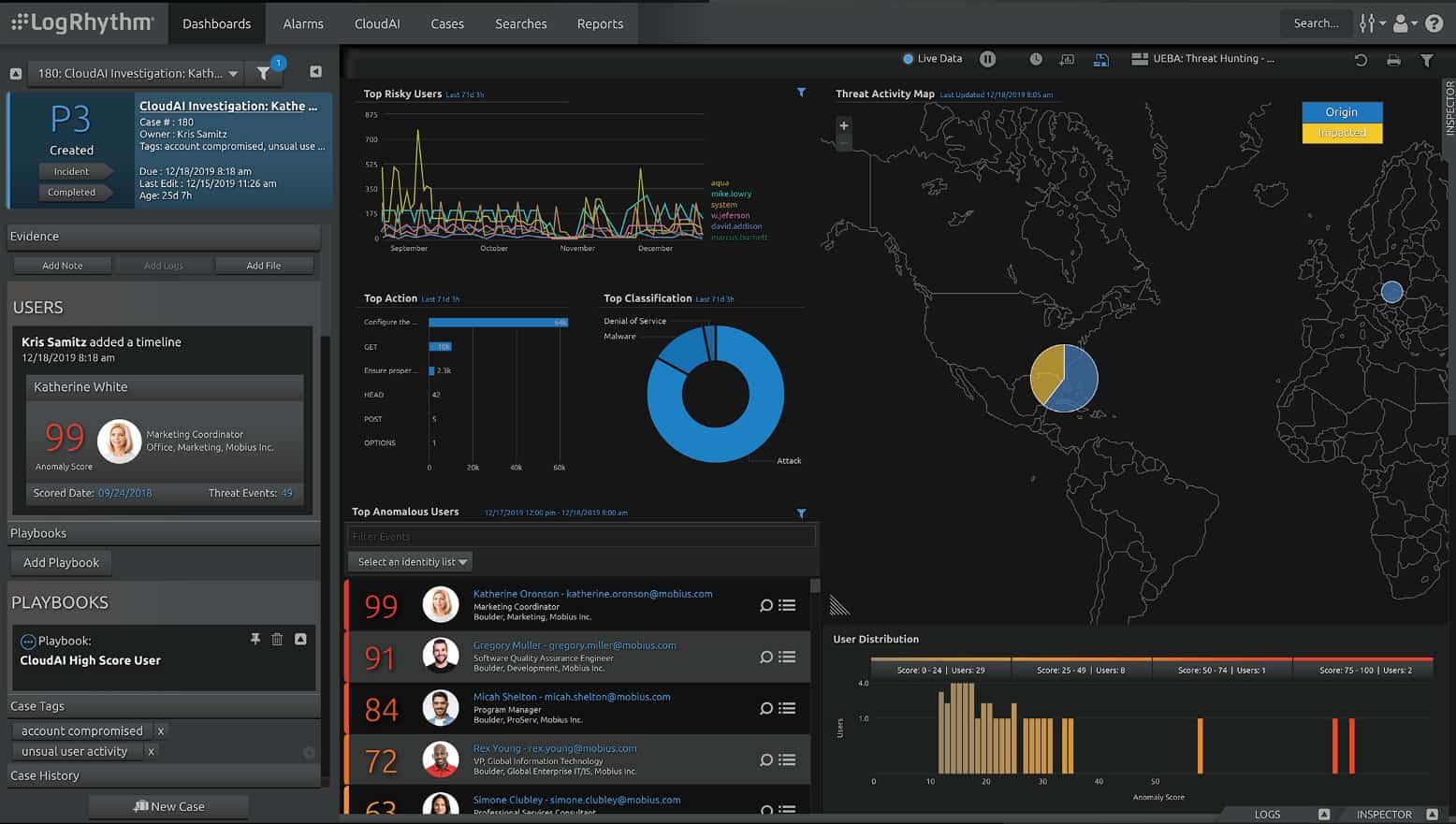
LogRhythm NextGen combines log management, security analysis, and endpoint monitoring, making it a powerful tool for identifying threats and thwarting breaches.
LogRhythm SIEM has a unique characteristic that makes it stand out from the crowd: its threat lifecycle management process. In order to make it effective in detecting and stopping threats, this company has developed a unique approach to tackle this task with end-to-end threat processing capabilities.
In other words, with this SIEM solution, all threats are managed in one place - from detection to response and recovery.
Additionally, LogRhythm uses data analytics to spot threats before they cause significant harm, if at all. SIEM shows administrators the detailed activities of all connected devices, allowing them to predict future threats based on experiences Anterior. Once they spot these suspicious behaviors, they can stop them before they happen, or as soon as they're detected.
Other features of LogRhythm:
All of this is accompanied by a SIEM solution that has, unsurprisingly, been named the best security information and event management software of 2019 by Gartner.
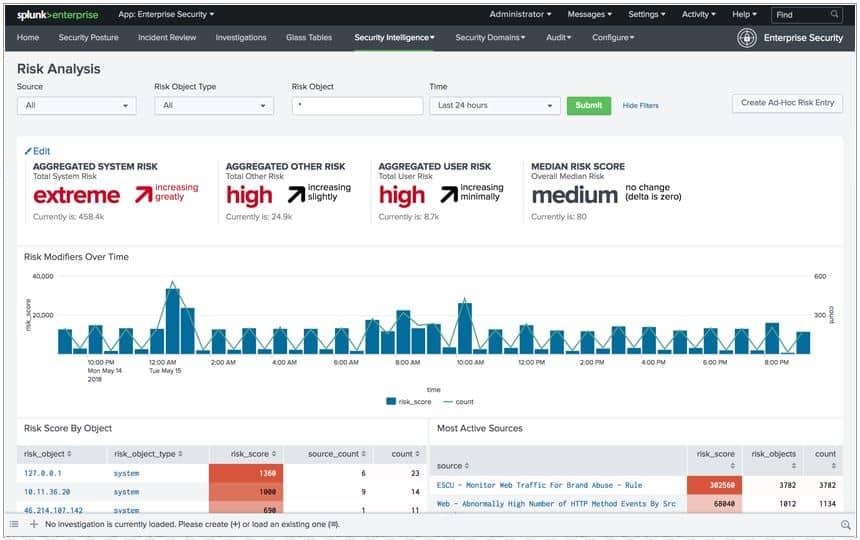
It is also another highly rated SIEM solution. A free version allows users to see the quality of this solution. While you can only index 500MB per day, that's enough to show why Splunk ES has earned praise.
Looking at a few more details, we have:
To be honest, the only complaint you can make about this SIEM is its price - the license could be out of reach for many SMEs.
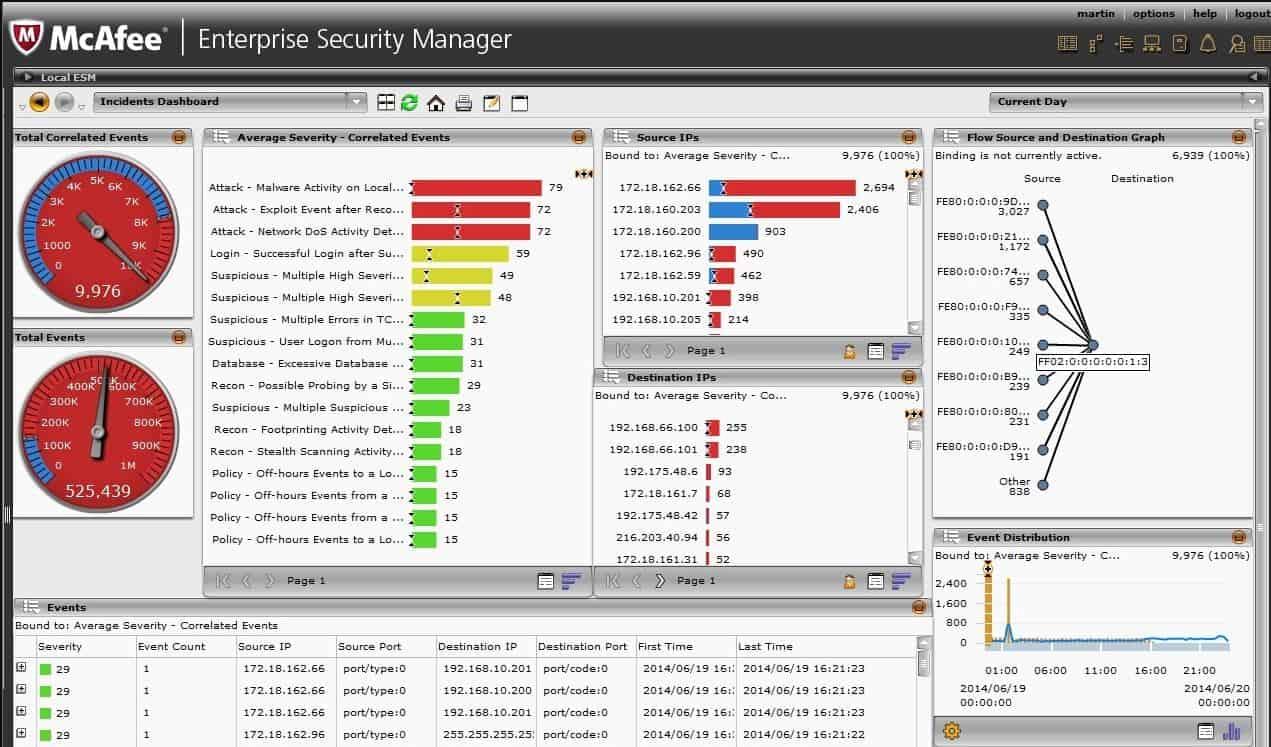
McAfee Enterprise Security Manager (SEM) comes from a well-established digital brand in antivirus and anti-malware that has been at the forefront of the industry for years. For skeptics, there's one fact they need to consider: McAfee's vast array of tools alone can serve as a data source, alleviating the problems of integrating and standardizing data from systems, networks, databases, and applications.
In addition to its own tools and products, McAfee also enables the standardization of data from products manufactured by its numerous companies. partners.
Other great features include McAfee ESM:
Again, the main advantage of this SIEM over other similar solutions is that McAfee has its own line of suites that can serve as log data sources - over 430, to be a bit more precise. This familiarity makes it possible to reduce the downtime spent on standardization, and therefore reaction times, which is appreciated in large networks.

Micro Focus ArcSight ESM is an enterprise security manager that has been around for nearly two decades. Over these years, it has continued to grow and evolve to become the great tool for analyzing and detecting networked malware that it is today.
This tool can claim to be one of the best SIEM tools on the market thanks to its ability to meet all scalability requirements, as it can now analyze 100,000 events per second!
Has a new supplier joined your network? No problem, the structured data in this SIEM can easily be used by third-party applications. In addition, theAcquisition of Interset, a security analytics software company, earlier this year, means the company aims to improve ArcSight's behavioral analysis and machine learning capabilities.
With all of these features, it's clear that ArcSight is the ideal SIEM tool for complex system-on-a-chip (SOC) environments and managed security service providers (MSSP). It's also a truly infrastructure-independent SIEM tool, whose services can be delivered through software, hardware, and cloud services like Amazon Web Services (AWS) and Microsoft Azure.
Additionally, distributed correlation allows for scalability, and as a result, ArcSight SIEMs can grow as fast and as big as they need to and reduce the time between mean time to detect (MTTD) and average time to response (MTTR).
Finally, the entire suite has a multitude of new user interface options, which means that ArcSight now comes with new graphics, dashboards, consoles, etc. that make fighting malware easy and enjoyable. Additionally, a large number of solutions and use case packages help build a solid defense that can then be shared (using rule sets and logic) between customers or businesses facing similar problems.
Overall, it's a great SEM tool!
Network administrators can address these malware issues in a number of ways, including:
But once you've taken all of these protective measures, that doesn't mean your job is done. You should continue to monitor your network and the defense strategy that protects it. You'll need to keep an eye out for signs of external threats and loopholes that could open up. In the event of an imminent threat, you need to develop an effective defense strategy to implement, based on real-time analysis of behavioral data gathered from your network.
To understand this tool, we first need to make sure we understand what security event management is.
Security event management is the field of computer and network security that manages the process of collecting, monitoring, and reporting on security events in software, systems, or networks.
For example, an SEM tool is an application that monitors system event data (typically stored in event logs), extracts information from it, correlates it, or translates it into actionable advice, and presents it to whom to whom. It does so through a preferred notification or alert method, and with the intention of taking additional steps to address reported suspicious or malicious issues.
The source of the recorded data may be security devices such as firewalls, proxy servers, intrusion detection systems (IDS software, NIDS, HIDS, etc.), and switches or routers.
At this point, we thought it would be a good idea to shed some light on these three closely related terms:
It should be noted that SEM and SEIM are used interchangeably and can both be in the form of software solutions, hardware devices, or SaaS services.
One of the main advantages of using an SEM tool is that it is an optimal solution to the “expenses vs expertise” conundrum. Here is the explanation:
Small businesses can't afford to spend a lot on their IT infrastructure, let alone have a team of competitive tech gurus on staff. And yet, 43% of SMEs [PDF] are the target of hacks and data breaches.
This means that an SEM becomes the optimal solution because it provides the services of a team of network security experts at a fraction of the price it would take to have them on board full-time. Indeed, once it is set up properly, it becomes a 24-hour defense system that reviews each recorded triggering event and waits to trigger the appropriate alert or response.
Armed with an SEM tool, you will be able to take care of it:
Our choices (yes, there are two, we couldn't choose between them) for the best malware detection and analysis tools for your network should be SolarWinds SEM for the superior, but affordable SEM tool, as well as LogRhythm NextGen SIEM Platform for a comprehensive defense system that has unique defense strategies.
There are 10 types of malware:
Static malware analysis consists of analyzing malicious code and evaluating its characteristics without running it.
Dynamic malware analysis is an evaluation method that requires malicious software to run so that its actions can be recorded.
This type of analysis should be done in an isolated environment, called a sandbox, to prevent the test from causing real damage to the host system.
Follow these steps to perform a full malware scan: