How do I encrypt files and folders?
Let's see the methods for encrypting files and folders in the Windows operating system:
There are various methods for encrypting files and folders in the Windows operating system. First, we'll discuss the methods that are built into the Windows operating system. These can be used easily by following simple configuration steps.
Apart from that, there are also various software tools that provide a strong layer of security for encrypting the database on our computer system. We'll explore these tools later in this article.
The basic built-in tools that are available for Windows include:
- MS Office document protection
- Encrypted file system (EFS)
- Bit-Locker
1) MS Office document protection for Windows
If we need to encrypt any of the MS Office documents to protect it from unauthorized access, we can use this method, which is very easy to apply. One can use this method to encrypt any file document like MS Excel file, MS Power Point file, MS Office, etc.
The steps are as follows:
1) First, open the document you want to protect or encrypt.
2) Go to the File menu and then select the option to encrypt the document as shown in the figure below.
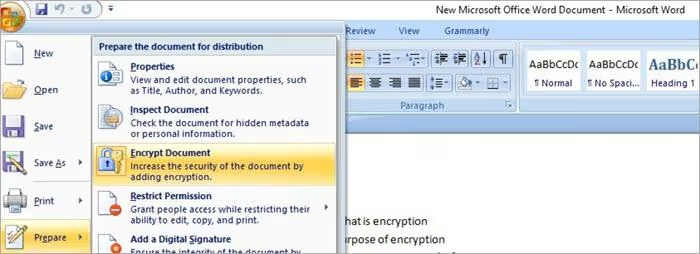
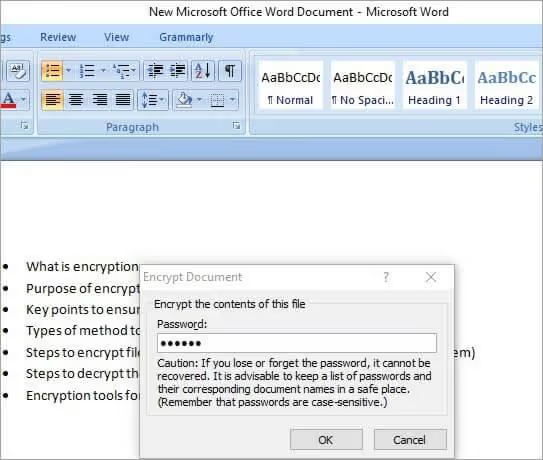
3) A dialog box will then appear, asking you to enter a password to protect the document, as shown in the figure below. Enter the password and re-enter the same password to confirm the correct password then click the OK button. The document is now protected, and this completes the file protection process.
4) If you try to open the document, it will first ask for the password and then only you can read or edit the document. In this way, one can encrypt the MS Office document and protect it from unauthorized access.
2) File system encryption
It is an encryption tool built into Windows, which is used to encrypt files and folders on NTFS drives. EFS allows individual files, folders, and directories to be manually encrypted instead of encrypting the entire drive. Encrypted files will only be available when the user who encrypted the file logs on to the system.
During this process, Windows generates the encryption key, which is automatically encrypted and stored locally on the PC. This process is not 100% secure and so we need to use a strong password to log in.
Steps to encrypt files on Windows using EFS
1) In Windows, first select the file or folder you want to encrypt and right-click on it.
2) Now, from the menu options, select the Properties option as shown in the figure below.

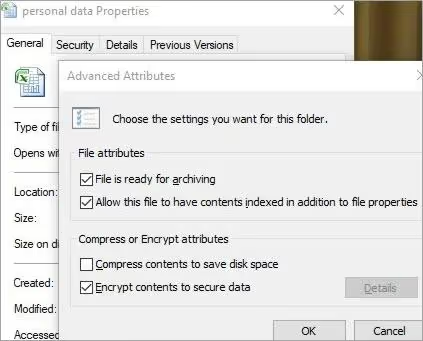
3) Select the Advanced button from the optional menu in the dialog box. The Advanced Settings Attributes dialog box then appears. In this box, select and check the “Encrypt content to secure data” option and click the OK button as shown in the figure below. Then click Apply.
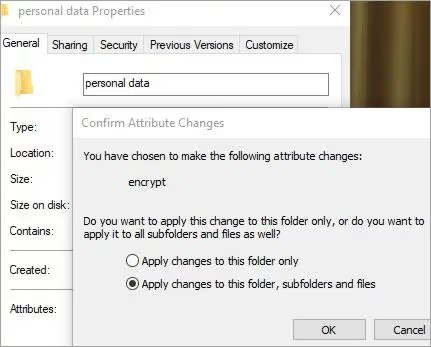
4) At this point, if you have chosen to encrypt a folder containing one or more files, a confirmation dialog will appear asking you to confirm the changes and to encrypt all files in the folder or specific files. Select the “Apply changes to this folder, subfolders, and files” option and click OK.
5) A pop-up message dialog will then appear, which shows the option to save your file's encryption key and certificate. If it disappears, you can also find it in the notification area of your operating system.
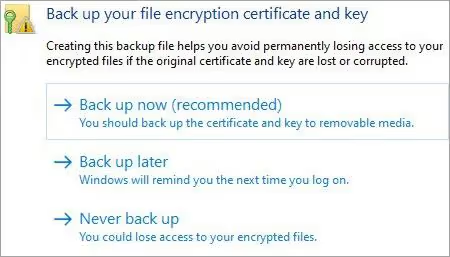
6) Plug the USB device into your PC where you want to back up. Then click on the “Backup now (recommended)” option as shown in the image below. Then click on next to continue with the process.
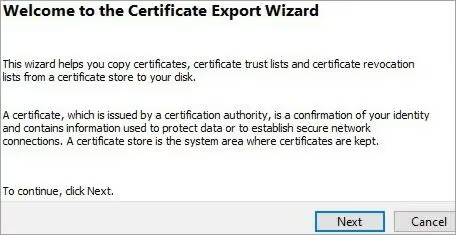
7) Click Next to generate the certificate as shown in the figure below.
8) Now check the.PFX file format to export the files and click Next again as shown in the image below.

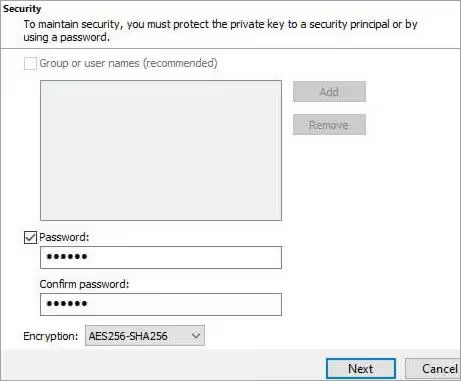
9) The password dialog now appears. Enter the password and re-enter the same password to confirm it, then click on the Next option to continue as shown in the screenshot below.
10) Open the USB device, then enter the name of the drive to be exported and click Save. The file will now be saved with the extension.PFX on your USB device. Click on the Next option to complete the process and then click on the OK button. Now you can safely remove the USB device and store it in a safe place.
You can use any storage device like a DVD, a portable hard drive, etc. to back up.
Steps to decrypt files and folders on Windows
To decrypt files and folders, we need to follow the same steps mentioned above up to step 4 and uncheck the “Encrypt content to secure data” dialog box. The files are then readable again. The passwords and the backup should be kept in a safe place so that we can easily recover them when needed to decrypt the files.
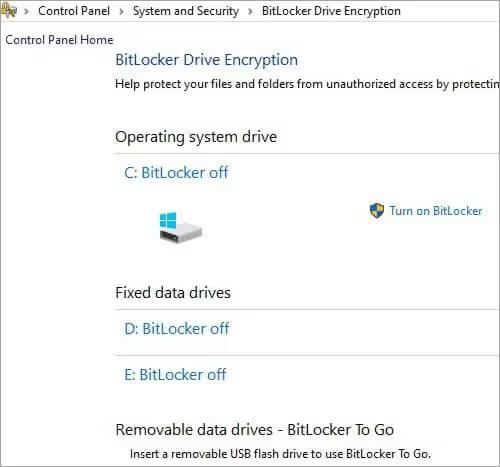
3) Bit-Locker
It is an encryption tool designed for Windows editions, but not for the Windows Home Edition starting with Windows Vista OS. It offers the encryption of entire volumes of data present on the hard drive or the external device inserted into the computer.
Characteristics and operation:
- It uses the AES encryption method, with an encryption block chaining mode and a 128- and 256-bit key.
- Bit-Locker is a tool that offers encryption not only at the software level but also at the hardware level using a TPM (Trusted Platform Module) chip.
- If TPM is not installed on your operating system, you can also encrypt files and folders using the software's built-in Bit Locker.
- To allow Bit Locker to encrypt the entire disk volume, the disk must be partitioned into two volumes. One boot partition is intended for the operating system and the other is kept unencrypted and will therefore be used to boot the operating system. Once partitioning is complete, the encryption process starts with configuring the USB sticks.
- There are various encryption modes in which we can use Bit Locker. To protect the operating system from physical attacks and malicious software at startup, the TPM hardware mode is used. The key that is used to encrypt the disk volume is encoded by the TPM chip and is only given to the operating system when the CPU is started for profit.
- The other mode is the USB flash drive mode. In this mode, the user inserts the USB device into the computer that has the connection key that allows the computer to start the operating system protected by the Bit Locker. For a correct authentication process, the startup key should also be provided with CCID cryptographic codes, which are used in combination so that the key is not stolen for unauthorized access.
- Once the system has successfully booted using these modes, it should be used with EFS to ensure additional encryption of files on the running operating system.
Thus, the Bit Locker alone is not a powerful encryption tool, as malicious viruses and boot managers can easily attack it. It is therefore suggested to use external software tools.
4) Encryption tools for the Windows operating system
There are several tools and software available on the market for encrypting files and folders in the Windows operating system, but here we are going to understand only some popular tools.
1) WINZIP
The WINZIP tool is used to encrypt data on computers like PCs, laptops, and servers in a compressed folder file with the.zip extension with password protection to provide high level security for confidential data files.
Features
- All file types, like image or video files with the extension (.png, .jpg, etc.) as well as MS Office files can be encrypted using this method. We can encrypt almost any type of file format using this method.
- The encryption methods used are the 128-bit and 256-bit AES encryption method. The numbers indicate the size of the encryption key, which is used to encrypt the data.
- It can also perform operations other than encrypting files, such as creating, compressing, and managing files.
Data file encryption steps:
Step 1: Open WINZIP and, in the action panel, click on the encryption option.
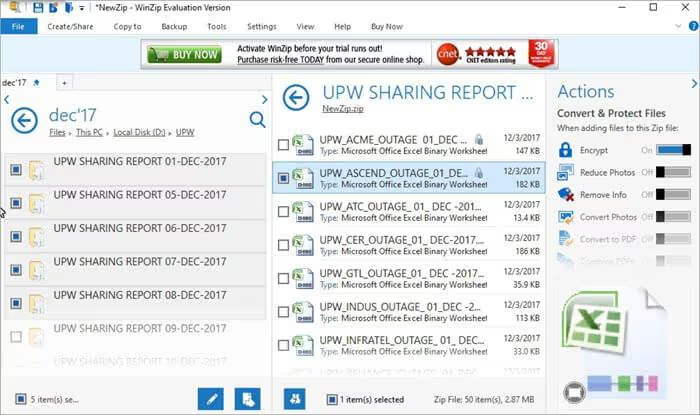
Step 2: Now, drag or browse the files you want to encrypt and compress into the central panel named Newzip.zip as shown in the figure below.
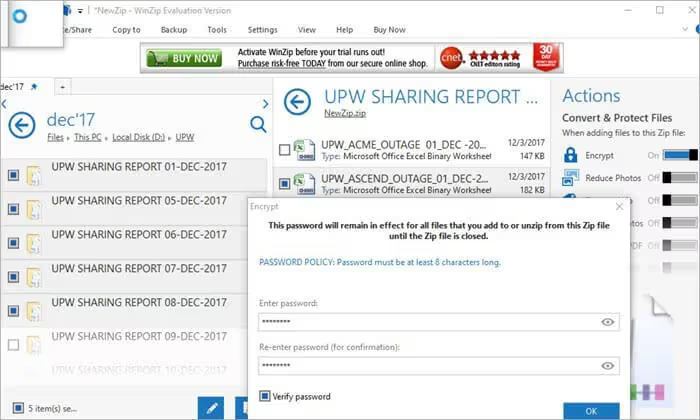
Step 3: Now, add the password to protect the file when the dialog box pops up to enter the password and enter the same password again to confirm as shown in the image below.
Step 4: Click the OK button. Then, the dialog box pops up and asks you to complete the compression procedure. Click OK and save the changes to complete the encryption as shown in the screenshot below.
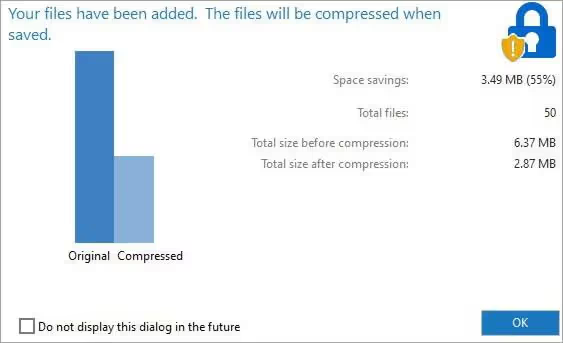
This completes the WINZIP encryption process. We can also perform other operations using the WINZIP tool such as converting the MS Office file to PDF and reducing the size of the data file or image file so that it can be easily sent by email, etc.
Pricing
WinZip 24 Standard: $35.34
Official URL: WINZIP
2) Crypto Expert
The Crypto-Expert tool is a much more powerful, secure, and reliable data security tool than other encryption tools built into the Windows operating system. It is therefore very popular in its use and also very easy to use.
Features
- It provides a secure safe for all data on your computer, hard drive, or laptops with fast on-the-fly operation.
- The tool ensures the security of all types of data stored on the PC, like various types of MS Office documents, PowerPoint files, image files, audio files, video files, and email backup data files.
- The encryption method used here is AES encryption with 64 and 256-bit encryption key algorithms, 3DES, CAST, and the Blowfish method.
- It can easily take the secure backup of the data using a USB stick and the only thing we need is the password to unlock the vault and after taking the backup immediately lock the vault. The vault can have an unlimited size, which can be greater than 10GB, and the user can create multiple vaults to secure the data.
- The vault can also be shared with a remote PC via the local network by providing the remote user with the unlock keys and cannot be accessed without a password.
- If the system is stolen, the data will remain secure and no unauthorized person will be able to access the secure personal data because the vault will appear as a normal Windows platform driver.
Pricing
Crypto Expert 8: $59.95
Official URL: Crypto Expert
3) VeraCrypt
This software supports the on-the-fly encryption methodology, which means that data encryption, including data files, folders, free space, metadata, image and media files, email backup, etc. is done automatically before the entire data is saved and decrypted automatically before being downloaded to a device, without the intervention of an external user.
Thus, no data can be read and decrypted without the correct combination of password and encryption keys by anyone who accesses the PC or system.
Features
- The data files are saved on the Vera Crypt volume and can be copied from there by the drag and drop method to the local PC and can be saved to RAM using the correct password and keys. The same goes for the decryption process.
- The Vera Crypt software never stores on the local disk the data requested from the Vera Crypt volume to be copied or opened on the local system.
- But it only stores the portion of the entire file that is requested to be seen or read in RAM temporarily, as it is only available to users for a certain period of time. So when we close the file and turn off the Windows operating system, the data will be removed from memory and will become encrypted again.
- To make them accessible, we need to enter the right password and keys over and over again. It is therefore a security software for Windows that is widely used for the encryption of sensitive and personal data.
- The encryption keys used by this software are AES, Serpent, and Twofish. Vera Crypt also offers some flexibility when it comes to encryption, as it can complete the process in partitions using the virtual partition method.
- In addition, it immunizes itself against new software introduced into the system, which may be viruses or malicious software that attack the security system.
- Besides Windows, it also supports MAC and Linux operating systems.
Pricing
Free
Official URL: Vera Crypt
4) Ax Crypt
It is a very lightweight software that is easy to install and use. It is a multi-lingual encryption software that can work with numerous languages like French, German, Italian, Spanish, and Russian, etc.

Features
- It uses a 128-bit and 256-bit AES encryption method for security purposes.
- It also offers cloud storage services to transfer confidential and personal data securely over the cloud network to the remote end server, which is connected to the cloud network through a third party.
- The software automatically creates Ax Crypt folders on the cloud network to securely transfer and share data. We can simply transfer the data by double clicking on it and save it using the same method.
- The best feature is that the software secures each of the unique files in a folder individually and also monitors new files added to the computer or system folder. When a new file is added, it secures it automatically and individually.
- Additionally, using this software, multiple files can be selected and secured at once with a single click.
- It also has a password management feature so that the user can manage them accordingly. It can also share the encryption keys with other users, and the encrypted files can then be viewed by other users on the network, but they need to have a different password.
- It supports the encryption of data files larger than 2 GB with the metadata preservation function,
- It is compatible with all versions of Windows OS and also with Android smartphones. Thus, these characteristics make its use popular.
Pricing
Free
Official URL: Ax Crypt
Summary.
The main objective of this tutorial is to understand the various methods available to encrypt confidential data and files or folders present on the Windows operating system in order to provide high-level security to the volume of data.
There are three built-in methods for encrypting files and folders on the system, which we have seen above using various examples and screenshots.
Apart from these options, we can also use some software tools to perform these actions. These tools are designed for this specific operation only and offer enhanced and improvised security features, as well as storage and sharing functions, in addition to the basic encryption process.
We've explained four of these tools above using screenshots and we've also shared the official URL so that anyone can download them if needed and gain a thorough understanding of these tools.
.svg)





