Discover how malware is evolving and the latest trends in cyber threats. Learn how to protect your devices from malware attacks.
Here is a summary of the most interesting malware statistics:
In 2020, 61 percent of organizations experienced malware activity that spread from one employee to another. In 2021, this figure rose to 74 percent, and in 2022, it reached 75 percent - the highest infection rate since the SOES survey began in 2016.
The increase in the spread of malware from employee to employee can be explained by a number of reasons; for example, phishing attacks are becoming more sophisticated and, at the same time, employees may be more distracted when working from home.
In its 2020 State of Email Security Report, Mimecast found that 51% of organizations experienced a ransomware attack that resulted in at least partial disruption of business operations. This figure increases to 61% of organizations in 2021.
In its most recent report, Mimecast changed its wording, so we cannot directly compare this year's results. The fact remains that in 2022, 35% of respondents blamed a low level of cyber resilience for the cyber attacks that disrupted their business.
Organizations around the world are reporting that ransomware attacks are impacting their businesses, but it seems that businesses American women are better and better prepared, with 47% of them having implemented cyber resilience strategies. However, in countries like the Netherlands, only 21% of businesses have a plan to deal with the cyber attacks they may face.
In its 2022 State of Cybersecurity Report, ISACA found that 69% of cybersecurity professionals feel that their organization's cybersecurity team is understaffed, up from 61% last year. Understaffing within organizations, including businesses and government, could create pressure on existing staff and lead to an increased risk of malware threats.
Nearly half (47%) said their organization was “somewhat” understaffed, while 15% said their organization was “significantly” understaffed. On the other hand, 34% of respondents indicated that their organization had “adequate” staff, while only 3% said they were “somewhat” or “considerably” overstaffed.
The demand for workers is also increasing year by year. Whether they are senior managers, technicians or collaborators, jobs in the cybersecurity sector are still not filled, as demand exceeds the growth in the number of workers with the required skills.

The SecureList report on The evolution of computer threats shows how Malwares-for-Hire continues to evolve. He points out that organized groups are increasingly developing cross-platform malware to compromise as many systems as possible on a target network.
This report also highlights vulnerabilities in Windows logging tools, which have seen a real resurgence recently (especially during the Log4J scandal, which prompted businesses to patch a large number of different applications).
Phishing sites are generally designed to look like the official version of other websites. PayPal is a commonly imitated site, for example, because accessing users' PayPal credentials can be very profitable for hackers. Banking sites and social networking sites are also fairly common targets.
According to the Google transparency report, 3.849 million warnings were posted to users who attempted to access sites deemed unsafe by the Safe Browsing category. as of August 7, 2022. Additionally, 1.6 million users saw warnings in their search results that the site they were about to visit could be dangerous.
If you look at the overall data, you can see that the number of warnings has dropped significantly over the past decade. This is unlikely to be due to fewer dangerous sites; instead, Google has improved its ability to identify and remove them from the results, which translates into an overall decrease in the number of warnings.
In 2020, the number of new malware attacks fell for the first time since 2015. However, according to the 2022 Cyber Threat Report From SonicWall, this was only a temporary drop, with malware attacks now standing at 10.4 million per year, about the same level as in 2018.
According to SonicWall, 5.4 billion malware attacks took place in 2021, which seems bad but actually represents a slight decrease compared to the previous year. We don't yet have the complete data for 2022, but the first six months saw 2.75 billion attacks, and if these numbers hold up, we'll end up having about the same number of attacks per year.
Domain generation algorithms, or DGA, allow malware architects to automatically generate a large number of domain names that then serve as meeting points to help monitor and collect data on active malware infections. DGAs complicate investigative and analytical efforts, making it difficult to shut down botnets.
Over 40 malware families employ DGA, including well-known malware like CCleaner, Emotet, and Mirai. SonicWall identified over 172 million randomly generated domains in 2019.
According to Kaspersky Labs, of all users of its mobile security product in the world, Iran has faced the largest number of malware attacks in the second quarter of 2022, the proportion of mobile users affected was 26.91%. This figure is in fact down by almost 10% compared to the previous quarter, when 35.25% of mobile phones were attacked.
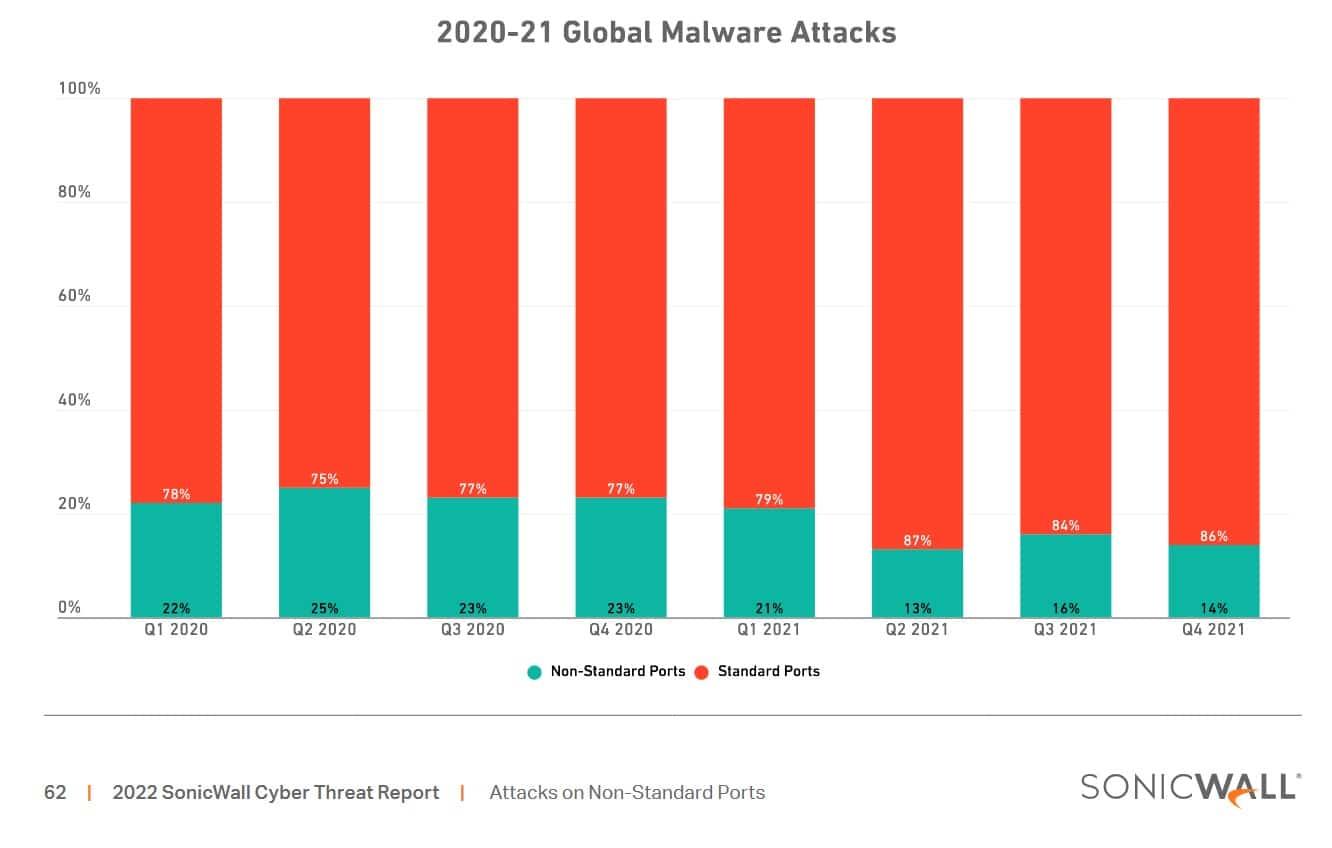
SonicWall's 2022 report found that attacks on the tens of thousands of non-standard ports available declined to nine percent in 2021. This is a significant drop compared to last year and in fact the lowest incidence rate since 2019. The vast majority of attacks still pose (and will likely remain) a problem for standard ports, such as HTTP (port 80).
SonicWall Half-Year Report 2022 shows that the quantity of ransomware has in fact declined from one year to the next, with an average of around 40 million attacks per month (compared to 50.5 million in the first half of 2021).
However, it is important to know that these numbers are already significantly higher than in previous years, largely due to the ransomware explosion that occurred during the COVID-19 pandemic.
SonicWall identified 270,228 “never-before-seen” malware variants in the first half of 2022 alone. This represents an increase of 45% compared to the same period last year, and an average of over 1,500 new variants per day. In March alone, nearly 60,000 new variants were discovered, setting a new record.
RECOMMENDED READING: The best malware detection tools
Their ubiquity on devices makes PDFs and Office files, such as Word and Excel documents, extremely popular as payload mechanisms for malware authors. During the first half of 2022, SonicWall found that Microsoft Office files were responsible for 10.28% of all malware, and PDFs were responsible for 18.27%.
The most common malicious file type remains the humble executable (.EXE) at 33.83%, followed by various script types (.JS, .PY, etc.).
Cryptojacking grew by more than 30% in the first six months of 2022, which is huge considering that it had already increased by 19% the year before. The chart below may seem to show that this is a downward trend, but SonicWall saw a similar “summer slump” last year before cryptojacking picked up at the end of the year.

The chaotic ups and downs of cryptojacking activity underscore how cybercriminals are responding to market demands. Malwares' aim has always been to get the best possible result (stolen information and money) with as little effort as possible. The increase in the use of malware website blocking technologies explains the increasing popularity of phishing sites, but cryptojacking is also an easy source of money for cybercriminals who, for all intents and purposes, follow the same principle as Wall Street brokers: “buy low, sell high.”
Although the cryptocurrency mining service Coinhive is legitimate, it was quickly co-opted by cybercriminals who installed it surreptitiously on websites in order to receive cryptocurrency income.
Initially launched in 2017, Coinhive voluntarily closed its doors in March 2019. SonicWall found that after Coinhive shut down, cryptojacking hits on its cybersecurity monitoring network fell by 78%.
In particular, Cerber is part of what is known as “Ransomware as a Service” or RaaS. Cybercriminals can hire others to launch attacks using Cerber malware, and receive around 40% of the ransom paid. In 2017, SophosLabs investigated 5 RaaS kits and found that some can be extremely cheap (less than 40 dollars), while others can exceed several hundred dollars to buy and use. However, they are highly customizable, and hackers seem to be operating their ransomware services with a surprising degree of professionalism.
Cerber resumed its most common ransomware signature crown during the first half of 2022. It had previously been relegated to second place by Ryuk, but the roles have been reversed again, with Cerber present in 43 million infections. SamSam, which was previously another top contender, was ousted from the top three by GandCrab, even though the group behind the latter officially closed shop in 2019.

Threat actors like to send malware attacks using encrypted SSL/TLS traffic. Encrypted channels make detection and mitigation more difficult, resulting in higher success rates for the malware packets in question. However, WatchGuard reported that in the first quarter of 2022, 60.1% of all detected malware were attacks of this nature, compared to 91% in the second quarter of 2021.
In 2021, a vulnerability was discovered in a very popular logging tool that allowed attackers to execute code remotely on affected systems. The magnitude of the problem (and its potential impact) was considerable, and while a fix was quickly put in place, the incident only further illustrates the need for regular software updates and a robust cyber resilience plan.
In June 2019, the University of California did the One of the newspapers after computer systems at the UCSF School of Medicine were involved in a ransomware attack by the hacker group known as Netwalker. A cure for COVID was the major project the drug team was working on at the time.
Netwalker planned to access financial records held by UCSF, which cited billions of dollars in annual revenue. The hacker group demanded the payment of a ransom of 3 million dollars. The attack was not entirely successful, but Netwalker still managed to negotiate the payment of a ransom equivalent of $1,140,895 in bitcoin by the drug group to repair the damage caused by the cyberattack. The BBC also reported that the hacker group was also responsible for two other cyberattacks targeting universities in 2020.
This university is far from being the only target. Higher education institutions across the United States were victims of these attacks, which also affected universities in Scotland, the Netherlands, and Canada.
Coveware noted that professional services were the most common ransomware targets in the second quarter of 2022, accounting for 21.9% of all attacks (up from 20.2% in the previous quarter).
This was followed by public sector organizations (14.4%), health organizations (10%) and computer services (9.4%). Financial institutions were significantly less popular this quarter, dropping from 8.9% to 6.4% in just three months.

In June 2019, the University of California Make the headlines after the computer systems at the UCSF School of Medicine were involved in a ransomware attack by the hacker group known as Netwalker. A cure for COVID was the major project the drug team was working on at the time.
Netwalker planned to access the financial records of UCSF, which has billions of dollars in annual revenue. The hacker group demanded the payment of a ransom of 3 million dollars. The attack was not entirely successful, but Netwalker still managed to negotiate the payment of a ransom equivalent of $1,140,895 in bitcoin by the drug group to repair the damage caused by the cyberattack. According to the BBC, the hacker group was also responsible for two other cyberattacks targeting universities in 2020.
Maastricht University also chose to pay €200,000 to the attackers in 2019, although this sum was later recovered. Meanwhile, the University of Utah paid $457,000 to decrypt data locked by ransomware, although in many cases victims don't actually regain access to their files after paying.

One of the main reasons why hackers seem to prefer ransomware over more traditional viruses and malware is for gain. Ransomware payments tend to fluctuate in size, but generally always on the rise. In the second quarter of 2022, the average payment was $228,125, with a median of $36,360.
Based on what we've seen so far in 2022, we can expect to see a few key things for the rest of the year:
We don't know what new threats may appear, or how the malware landscape may evolve. As major security companies have reported in the past, a considerable amount of business tends to increase in the fourth quarter most years, which is often associated with the holiday shopping season.
As always, hackers tend to be reactive instead of proactive, looking for ripe fruit whenever possible, or easily exploitable vulnerabilities in the systems where they can be found. They tend to change tactics only when their efforts are no longer profitable.
It is also difficult to ignore the ever-present danger posed by State-sponsored malware attacks, which are rarely motivated by profit and tend to have political reasons. These attacks are likely to increase in 2023, with all eyes on Russia, China, and North Korea.