Learn about three effective methods for detecting hidden images in steganography. Improve your image reading skills. Read the article!

Steganography represents the subtle art of concealing information in a variety of digital media.
This name comes from the combination of the Greek words “steganos” (which means hidden) and “graphein” (which means writing).
Unlike cryptography, which visibly encodes messages, this technique masks their very existence, making them invisible to unauthorized observers.
This technology operates primarily by exploiting the less significant parts of digital files: reverse image search can be used to detect steganographic images by identifying other versions of an image and verifying their origin.
The applications of this technique range from intellectual property protection to secure communication, while raising important questions in cybersecurity subject. Its ability to hide sensitive data can in fact be used for malicious intentions, in particular for the distribution of malicious software.
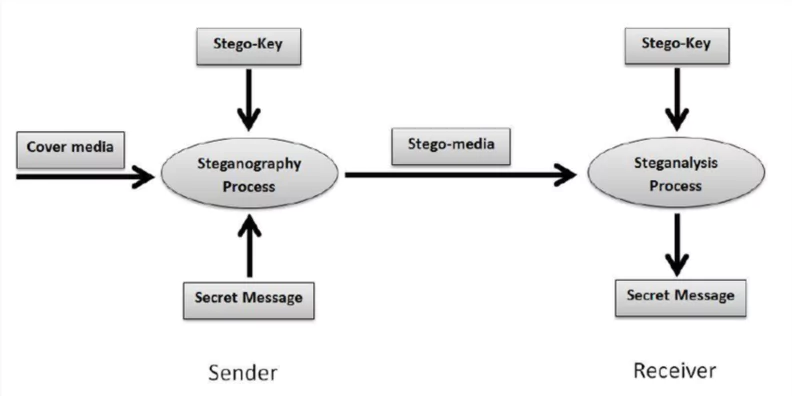
Modern steganography is based on a sophisticated process of concealing information in various types of digital media. Its effectiveness depends on its ability to exploit redundant areas of data without altering the perceptible quality of the support.
The process is divided into four essential phases:

Insertion techniques vary according to needs:
Recent advances, including the use of artificial intelligence and quantum steganography, open up new perspectives while maintaining a delicate balance between insertion capacity and discretion. This technology, while powerful, faces constant challenges in terms of detection and robustness.
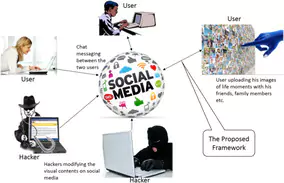
Steganography, the art of hiding information in images or audio files, is finding fertile ground on social networks. These platforms, where users share millions of images and videos on a daily basis, can become unintended vectors of malicious content. Hackers often exploit this technique to hide malware or sensitive information in seemingly innocent images.
It is therefore crucial to verify the origin and source of the images you share on social networks. Using reverse image search tools like Google Images or TinEye can help you trace the source of an image and detect any suspicious changes.
By being vigilant and adopting best practices, you can avoid spreading potentially dangerous content and protect your online safety.
Modern steganography is revolutionizing the protection of digital copyright. Invisible watermarks can now contain up to 2,048 bits of information in a 1080p image without visible alteration, allowing the integration of complex signatures.
Current techniques offer:
This technology, adopted by more than 80% of major digital publishing houses, demonstrates a leak detection rate of 99.7%.
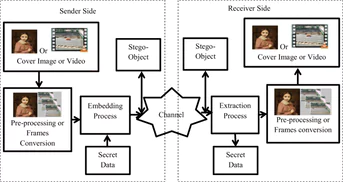
Modern communications use sophisticated techniques:
This approach, used in particular by journalists in sensitive areas, offers proven protection with a detection rate of less than 0.01%.
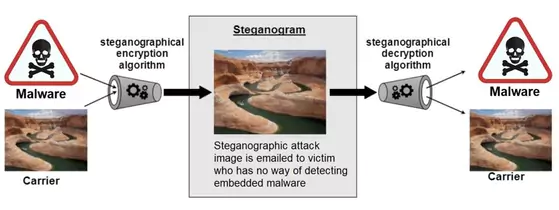
Modern forensic analysis integrates advanced steganographic detection capabilities. Current tools can identify Malwares hidden with an accuracy of 99.3%, even in files compressed up to 90% of their original size. Reverse image search can also help identify specific objects in images, using computer vision to retrieve relevant data.
Detection is based on several key markers:
This technology, adopted by 73% incident response teams (CERT), makes it possible to detect malicious payloads as small as 128-bit.

The military field uses ultra-sophisticated steganographic techniques allowing the transmission of critical information with a reliability of 99.999%. Modern systems support:
These systems, deployed in more than 40 countries, guarantee total concealment of strategic communications while maintaining an effective bandwidth of 1.2 Kb/s in degraded conditions.
Steganographic techniques are revolutionizing digital marketing With QR invisible codes capable of storing up to 4,096 characters while remaining undetectable to the naked eye. Modern campaigns achieve engagement rates of 37% superior thanks to these technologies.
Campaign monitoring is carried out via:
The fight against financial counterfeiting uses microscopic steganographic markers with a density of 2,400 dpi. Modern banknotes incorporate up to 12 levels of steganographic protection, with a fake detection rate of 99.97%.
Banking systems use:
This infrastructure, deployed in 92% major financial institutions, makes it possible to secure more than 2 trillion of annual transactions.
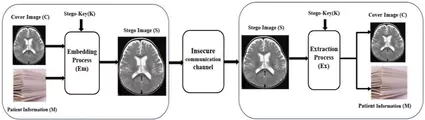
The medical sector is exploiting these techniques to protect patient data in diagnostic imagery. Current systems allow the integration of up to 16 KB of patient data in a standard X-ray while maintaining a diagnostic quality of 99.99%.
Medical protocols include:
The adoption rate in health institutions reached 78%, with proven effectiveness on more than 2.3 billion of medical records.
The academic community uses steganography to protect the integrity of research data. Current systems make it possible to detect plagiarism with an accuracy of 99.8% thanks to unique signatures on 1024 bits.
Educational innovations include:
These systems, adopted by 84% of major universities, have made it possible to reduce cases of academic fraud by 73% since their implementation. Combining these technologies with artificial intelligence opens up new perspectives for securing and authenticating sensitive data in all these fields of application.
The identification of a picture On the websites uses several methods of analysis. Les search tools suchlike TinEye and Google Lens allow you to find the source of an image and the analysis of copyright via digital watermarks allow to authenticate the provenance Of Contents.
The data Exchangeable Image File Format reveal accurate information aboutCamera used, with a precise GPS location at 3-5 meters. Reverse image search can be an alternative to textual keywords to find information related to images. Les photographers professionals use these informations to protect their photographs.
La Search by image upon Internet, in particular via the search engine Google Images, allows you to find similar images and their first appearances on the Web. This approach, combined with digital signature analysis, helps to trace the complete history of a file.
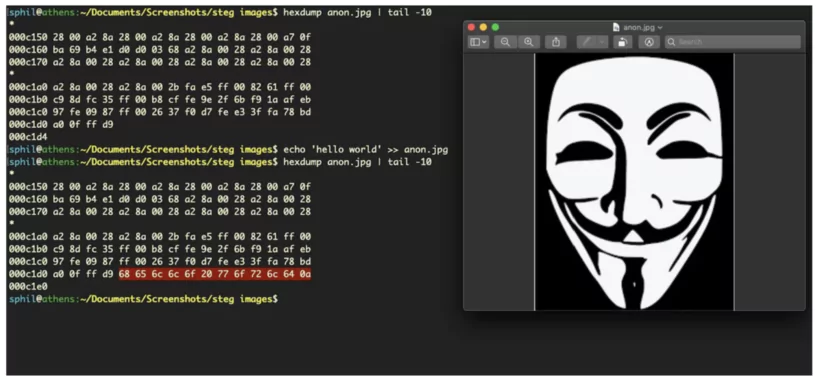
Les social networks systematically modify the data Originals of pictures. On these sites, transformations include:
The identification of springs therefore requires a rigorous methodology that respects confidentiality standards and uses the right search tools.

Les EXIF metadata (Exchangeable Image File Format) is technical information embedded in digital images. They include details such as camera model, date and time of shooting, and even geographic location.
This metadata can also be used to hide information via steganography.
To detect the presence of steganography in the EXIF metadata of an image, it is possible to use reverse image search tools such as Google Images or TinEye. These tools make it possible to compare an image with others on the web and to identify anomalies or suspicious changes.
By carefully analyzing EXIF metadata, you can identify signs of manipulation and thus protect your images and personal data.
By adopting these practices, you are increasing the security of your digital content and contributing to a safer online environment.
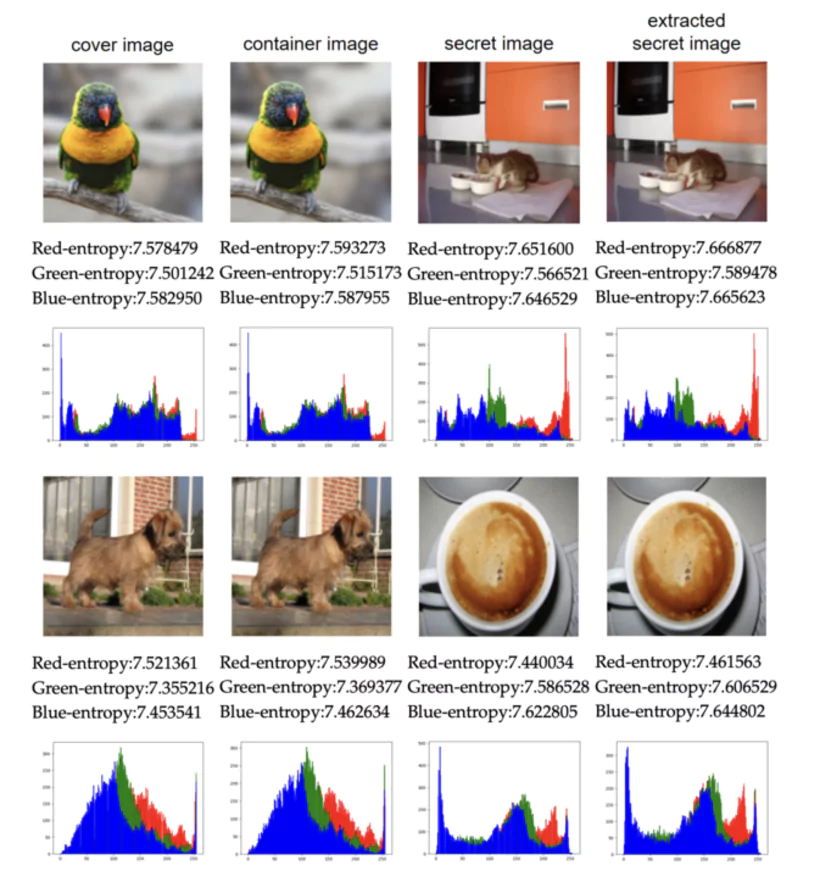
Image steganography is the most successful concealment technique to protect your files. The LSB method transforms the minor bits of the pixels with a precision that makes it possible to mask up to 10% additional data.
Key benefits include:
This approach makes it possible to effectively protect your data while maintaining the original appearance of your pictures. Reverse image search can be used to verify the integrity of steganographic images, by identifying alterations or altered versions of the original image.
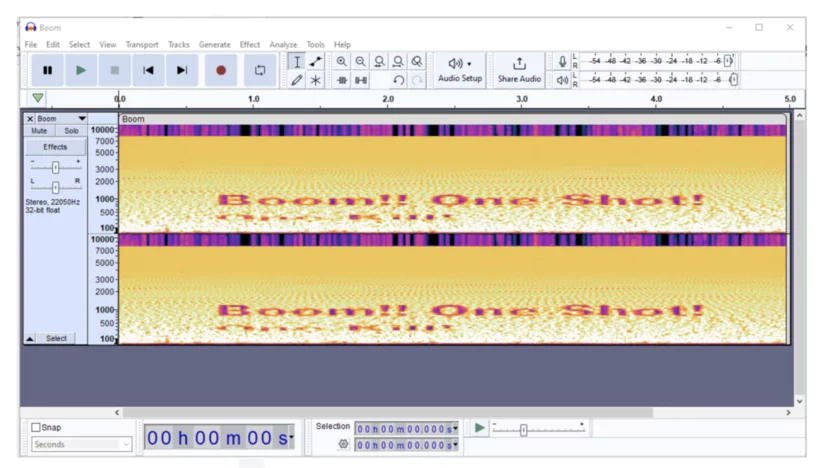
The insertion of contents In the files audio exploits the limits of human hearing. This technique uses echo and phase modulation to create invisible storage spaces in the sound signal.
The audio signal is modified on:
The video format offers an ideal terrain for concealment thanks to its numerous successive frames. Discrete cosine transformation (DCT) makes it possible to integrate informations in each image without altering visual quality.
The analysis of Contents Video shows:
This method is particularly excellent in the protection of rights on sharing platforms.
The art of concealment in text is based on subtle and imperceptible changes. Variations in spacing, formatting, and the use of similar characters create invisible storage spaces in your documents.
Textual techniques include:
The protection of data transiting on the networks makes use of unused fields in communication protocols. This approach ensures the secure transmission of informations sensitive through the Web.
This method requires tools specialized for analysis and detection, making it particularly effective for secure transmission.
Modern approaches combine several methods to increase the security of your Contents. The use of Fourier transformation and artificial intelligence greatly improves discretion and resistance to analyses. This synergy between different techniques guarantees optimal protection of your files sensitive.
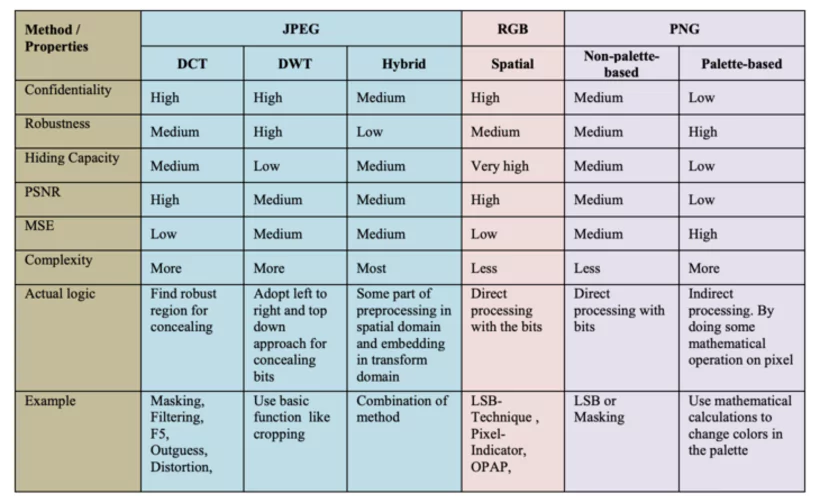
Les tools of steganography such as F5 and HUGO transform the protection of Contents. These Methods analyze each picture for optimal concealment of informations.
La database Ofpictures recommended includes:
THEutilizing with a minimum resolution of 1080p On the file source provides effective protection. The photographer must respect an insertion ratio of 5 to 10% while maintaining visual quality with a PSNR greater than 40 dB.
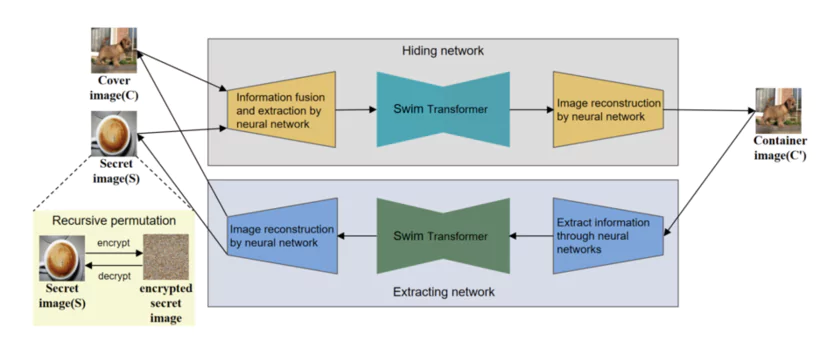
Securing requires several steps:
Respect for tricks of protection and standards in force guarantees ethical use on websites and social networks. The documentation of Methods and a constant watch for the news functionalities ensure lasting protection of Contents digital.
Modern steganography is redefining the standards for the protection of digital content. Its effectiveness is based on sophisticated algorithms capable of hiding up to 8 KB of data in a simple image, while maintaining flawless visual quality.
This technology is no longer reserved for experts: current tools allow accessible and effective protection of your digital creations. However, its use requires a thorough understanding of security issues and best practices to ensure optimal protection of your content in compliance with ethical and legal standards.
The combination of steganography with artificial intelligence and quantum encryption opens up promising new perspectives for the future of digital data protection, heralding an era in which content security is becoming invisible but omnipresent.